Tidal’s Adversary Intelligence team continuously identifies and processes public sources that contain mappings to the MITRE ATT&CK® knowledge base. Our collection mainly involves public threat research & intelligence reports, government advisories, and blogs focused on incident & campaign responses/investigations and malware technical analysis. The Making Waves series takes a data-driven approach to spotlighting ATT&CK techniques that are “trending” in public reporting (or alternatively, techniques that tend to be cited infrequently).
Each edition will enrich the spotlighted techniques with context based on recent threat intelligence. We encourage supplementing this with further context from Tidal’s free Community Edition, which aggregates many relevant supporting resources into a single hub, including defensive & offensive security capabilities from vendors in our Product Registry, detection Analytics, and ATT&CK Groups, Software, Campaigns, & Data Sources. A great place to start pivoting is the Preview or Details page for a technique, such as the one for LSASS Memory (T1003.001) here.
Steal Web Session Cookie (T1539)
This Credential Access technique continues to be referenced often in recent months, largely in relation to information & credential stealing malware (“infostealers”). Tidal has covered trends in the infostealer landscape and the techniques associated with this category of malware heavily recently, including in our blog series (see Part 1 & Part 2) and in our 2023 Threat Landscape webinar.
In February, Steal Web Session Cookie was referenced in three reports on relatively new infostealer strains: Cyble Research and Intelligence Labs’ analysis of Vector Stealer, a deep dive into Stealc stealer from Sekoia.io’s Threat & Detection Research Team, and Bitdefender’s discovery of a campaign associated with S1deload Stealer. The technique was referenced six more times in other recent reports during the prior quarter that mainly focused on new infostealers like Erbium or updates around well-established stealers like RedLine.
For Part 2 of our blog series, Tidal’s Adversary Intelligence team aggregated publicly available ATT&CK techniques associated with 19 recently active infostealer families. A technique matrix version of this dataset can be accessed in Tidal’s free Community Edition here. Our analysis of this data indicated that T1539 was the overall most frequently cited technique associated with this set of threats. Infostealer developers appear especially focused on stealing cookies, which can be used later to bypass multi-factor authentication security countermeasures. We dived deeper into details of this technique’s recent implementation and potential defensive countermeasures in a recent blog here.
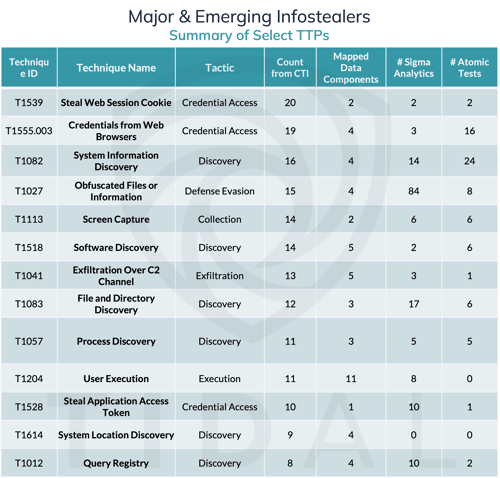
A summary of select top techniques from Part 2 of our infostealer threat landscape blog series, which identified T1539 as the technique most often associated with a large set of recently active stealer malware. This data derives from the Major & Emerging Infostealers technique matrix available in Tidal’s free Community Edition.
Input Capture: Keylogging (T1056.001)
Keylogging is another technique used for Credential Access (and for Collection purposes), and while it too has been associated with infostealers, it was recently referenced in relation to other types of threats. The DFIR Report team provided a detailed investigation report about an intrusion where the primary goal appeared to be information collection via a keylogger and exfiltration of the logged data. Actors, linked by The DFIR Report researchers to the Iranian-government-associated OilRig group, used a renamed version of AutoHotKey, an open source scripting language, and a PowerShell script to collect data from the KeypressValue registry key. Separately, the CYFIRMA Research team provided analysis on a new post-exploitation framework known as EXFILTRATOR-22, believed to be linked to ex-affiliates of the LockBit 3.0 ransomware gang, that performs keylogging by polling Windows API functions, while ESET researchers reported on a campaign to deliver FatalRAT, a remote access trojan capable of capturing keystrokes, which appears to target Chinese-speaking users in East & Southeast Asia via download through legitimate web search result ads.
While relatively light on procedural details, newly released information surrounding two recent LastPass security incidents highlights the serious potential impact posed by threats involving keylogging techniques. According to the LastPass incident report, threat actors compromised the personal computer of a DevOps engineer who possessed privileged access and implanted keylogger malware, which enabled the actor to “to capture the employee’s master password as it was entered, after the employee authenticated with MFA, and gain access to the DevOps engineer’s LastPass corporate vault”. Ultimately, the actor accessed cloud-based LastPass data during this incident, including cloud backups and encrypted and unencrypted customer data. Researchers highlighted other instances of T1056.001 use in recent months in association with a range of advanced persistent threats (“APTs”), including actors targeting Japanese political entities, financial & legal companies in Europe & the Americas, and South Korean government & military organizations.
Drive-by Compromise (T1189)
Drive-by Compromise is an Initial Access technique whereby an actor gains illicit system access through a user visiting a website during the normal course of browsing. Adversaries can compromise the website in a few different ways, including code injection into the site, abuse of built-in web application interfaces, or by purchasing advertisements through legitimate ad providers that ultimately point to sites hosting malicious content, an implementation that has been especially prevalent in recent times.
In February, we identified four reports that referenced this technique, representing a recent monthly high point, but this figure likely understates the significant uptick in this technique’s use in recent times. Abuse of legitimate web search ads (often referred to as “malvertising”) is a well-established technique that has witnessed a dramatic resurgence since late 2022, being used to deliver a wide range of highly impactful malware, including loaders like IcedID (themselves a serious threat used to deliver more impactful threats), remote access trojans, highly active infostealers, and even ransomware.
We touched on T1189’s frequent use as an initial access technique for multiple notable infostealers in both parts of our infostealer landscape series. Part 1 highlighted how many recent malicious ad campaigns particularly mimicked software used in enterprise environments, underscoring a rising infostealer and drive-by compromise threat to businesses specifically, while Part 2 offered a few recommendations for mitigating risk posed by this trending access vector, including user awareness and promotion & enforcement of responsible device use policies.
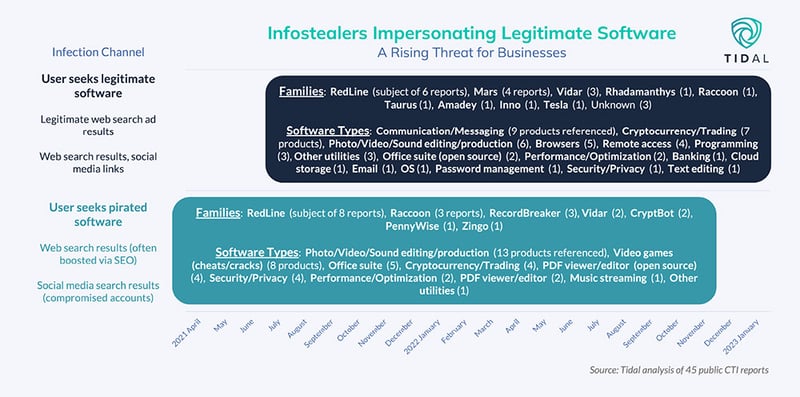
This infographic, from Part 1 of Tidal’s infostealer threat landscape series, highlights the rising threat posed by Drive-by Compromise as an initial access vector for infostealer infections relative to enterprise environments specifically.
Query Registry (T1012)
While this Discovery technique is observed relatively regularly (and has been historically associated with a large number of threats), we recorded a relative increase in references during the past two months, with references reaching a recent monthly high point in February.
Mirroring the range of adversaries traditionally known to use this technique, references last month came from reports involving a range of threat types, including a new ransomware strain (MortalKombat) and a new campaign linked to a known family (GlobeImposter), a backdoor possibly linked to the North Korean APT Lazarus Group, and a new infostealer believed to be derived from popular existing families Vidar and Raccoon Stealer. The technique also represents one of the many Discovery techniques that are common among the 29 groups & families included in the continually updated Ransomware & Data Extortion Landscape technique matrix available in Tidal’s Community Edition, having been recently associated with four specific ransomware families. On a positive note, the T1012 Technique Details page highlights that there are a total of nine vendors from Tidal’s Product Registry with Test, Detect, and Protect capabilities aligned with this technique, as well as four Data Sources providing potential visibility into its use and 10 open source detection Analytics from the public Sigma rule repository.
Command and Scripting Interpreter: Unix Shell (T1059.004)
This Execution technique refers to use of Unix shell commands and scripts to perform adversarial behavior. Although the Unix shell is the primary command prompt on Linux and macOS systems, this technique is not observed too regularly in public reporting simply because reporting volumes around Linux & macOS threats remain relatively light. The two references to T1059.004 last month therefore provide a relatively rare chance to spotlight a technique unique to these environments.
One observation came from SECUINFRA Falcon Team’s analysis of the ESXiArgs ransomware. While reporting on this threat first emerged last summer, ESXiArgs activity took a sharp upswing in early February as adversaries commenced automated exploitation of a two-year-old vulnerability, CVE-2021-21974, to achieve initial access into target systems: internet-facing deployments of VMware ESXi, a hypervisor used to deploy virtual machines on Linux servers. The SECUINFRA report highlighted how ESXiArgs’ encryption functionality is implemented via the encrypt.sh script run in bash, one of multiple variations of Unix shells. The report in fact highlights multiple ATT&CK techniques that are not regularly seen in public reporting, including another Linux/macOS-specific technique, Clear Linux or Mac System Logs (T1070.002), as well as Internal Defacement (T1491.001), which coincidentally was referenced again last month in relation to an entirely separate campaign.
The other T1059.004 reference in February provides an opportunity to highlight a macOS-specific threat. The reference came from CrowdStrike’s report about its discovery of I2Pminer, a malware used to deliver the open source XMRig cryptomining software on macOS systems specifically. In this case, the dropper component of the threat utilizes the /bin/sh variation of the Unix shell to execute subprocesses designed to make the malware appear like a legitimate application that the user intended to download. It also uses bin/sh and bin/bash to execute scripts that drop the XMRig payload and a payload for the Invisible Internet Protocol (I2P) tool used to hide XMRig network traffic, respectively. CrowdStrike’s report provided full command line execution details, as well as details around other observed behaviors like I2Pminer’s masquerading activity, which may provide opportunities for detection.


