Welcome to a new series that spotlights MITRE ATT&CK® techniques observed by Tidal’s Adversary Intelligence team across a wide cross-section of public threat research & intelligence reporting over the past month. We aim to spotlight less-frequently cited techniques, the adversaries recently associated with them, and – most importantly – some ways that security teams can reinforce relevant defenses.
We’ll take a data-driven approach to determine which techniques to spotlight and use Tidal’s Community Edition to enrich them and pivot among various related defensive resources. Moving forward, we expect to be able to share more granular metrics (e.g., percent change) in future iterations. We welcome feedback on what else you’d like to see!
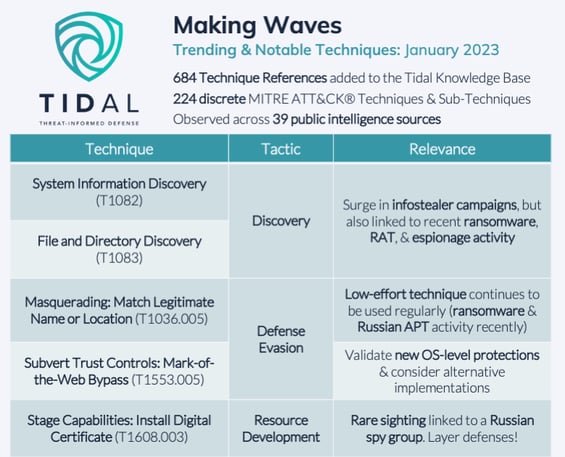 In January, our Adversary Intelligence team added 684 technique references to the Tidal knowledge base, which were observed across 39 sources, mainly public threat research & intelligence reports, government advisories, & blogs. In total, these references covered 224 discrete techniques, or 38% of the 594 techniques & sub-techniques currently included in the ATT&CK knowledge base. Let’s dig further into a few trending or otherwise notable techniques:
In January, our Adversary Intelligence team added 684 technique references to the Tidal knowledge base, which were observed across 39 sources, mainly public threat research & intelligence reports, government advisories, & blogs. In total, these references covered 224 discrete techniques, or 38% of the 594 techniques & sub-techniques currently included in the ATT&CK knowledge base. Let’s dig further into a few trending or otherwise notable techniques:
System Information Discovery (T1082) & File and Directory Discovery (T1083)
Both of these techniques are cited in threat reporting quite often, but they are worth spotlighting due to how frequently they were observed in recent months alone. We added 53 references to these techniques to our knowledge base last month from a total of 23 sources. The surge is driven in part by reporting on infostealer campaigns linked to a range of families, including Rhadamanthys, Aurora, LummaC2, and Titan, although reports about a range of other categories of threats were also observed, including ransomware, Remote Access Trojans (RATs), and espionage actors.
It makes sense that these techniques are observed often, since adversaries interested in victim data, whether for financial gain, espionage, or encryption (or some combination of motivations), usually need to locate where exactly it is stored on victim systems. Generally, however, Discovery techniques present challenges for detection, since threat actor discovery in many cases will appear like benign behavior, and for protection & mitigation, since legitimate users must also be able to regularly find and access their files too. 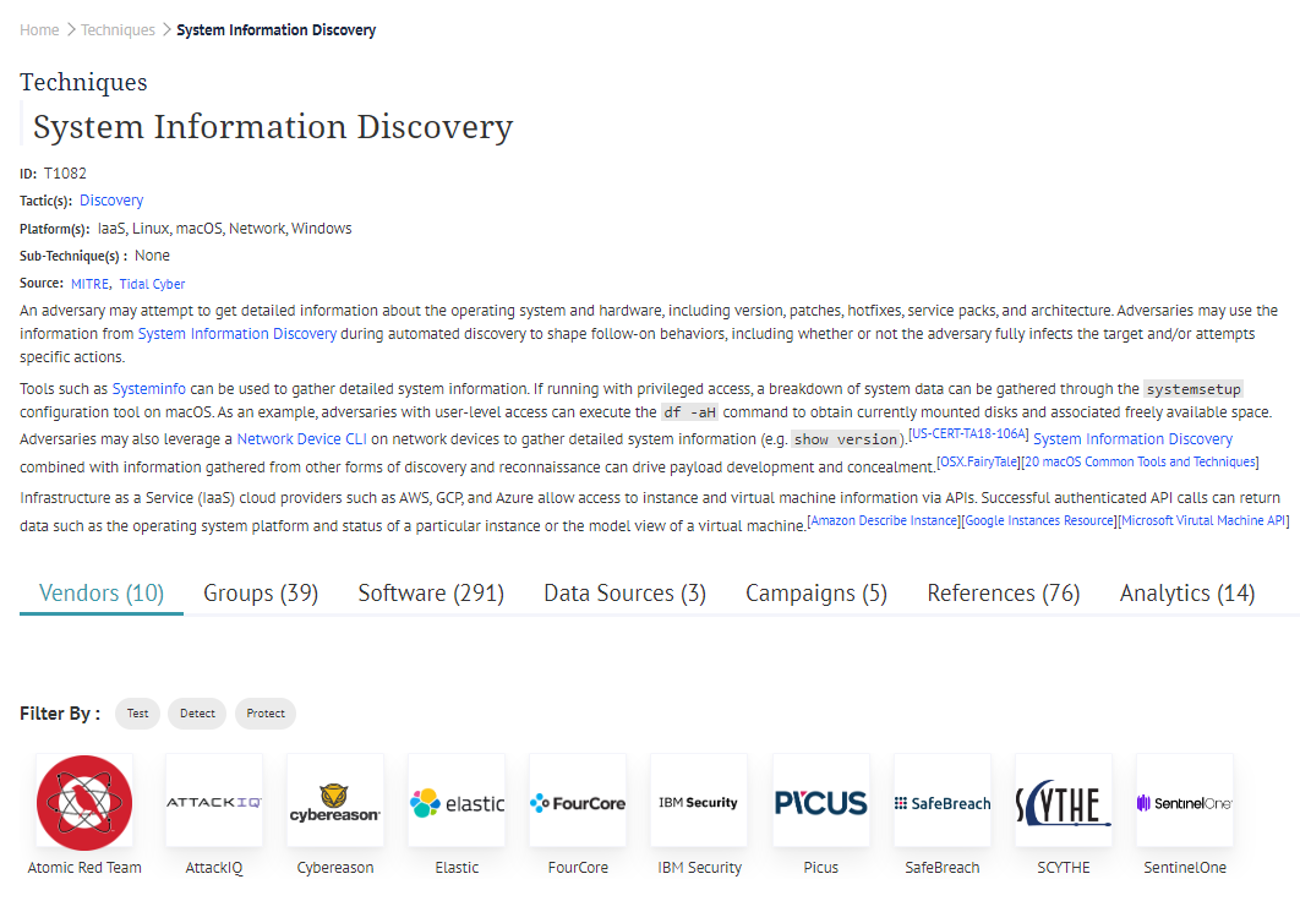
Defenders looking for detection opportunities for implementations of T1082 or T1083 may consider correlating on multiple discrete events taking place over a given time frame, focusing first on procedures known to be used by active adversaries. For example, we recently wrote this Atomic test which simulates System Information Discovery procedures recently used in the wild by Aurora Stealer. Rather than attempting to detect or alert on any single one of these WMIC commands, which may suffer from noise produced by legitimate applications that surface system information, defenders could consider correlating on the execution – in rapid succession – of the three commands specifically used by Aurora Stealer (samples usually show them happening within ~1 second of each other).
For more around infostealer techniques & trends, check out our living Major & Emerging Infostealers matrix or our recent blog series: Part 1 gave background on the threat landscape, while Part 2 dove further into top stealer techniques & associated defenses.
Masquerading: Match Legitimate Name or Location (T1036.005)
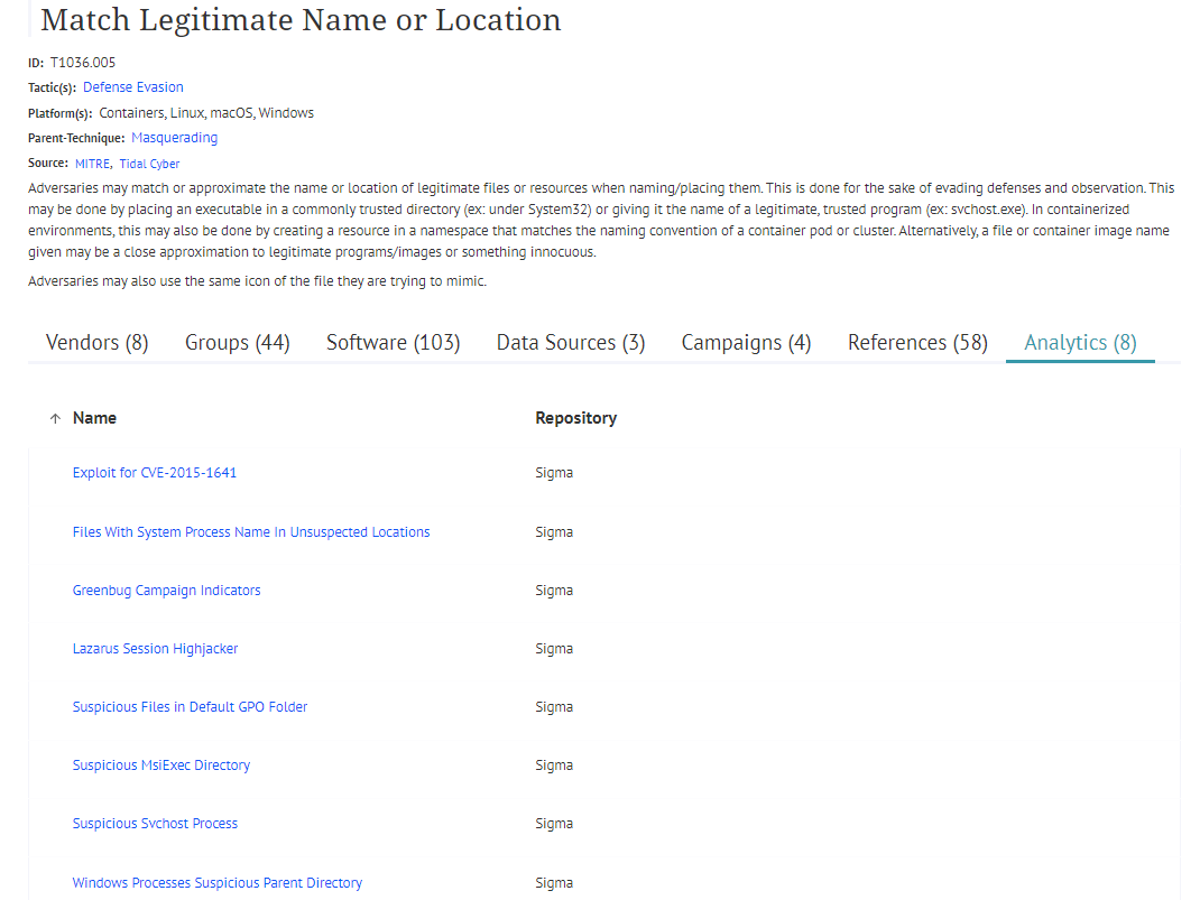
This Defense Evasion sub-technique, a child of the Masquerading technique, describes adversary efforts to blend into the victim environment by mimicking (or approximating) the name or location of legitimate resources within the environment. While it is not a totally uncommon technique (44 Groups and 103 Software from the ATT&CK knowledge base currently map to it), we don’t see it called out in threat reporting extremely often; however, last month we added five reports to our knowledge base that reference T1036.005, a good reminder that this relatively low-effort technique continues to be used regularly in real threat activity. Last month, vendors reported observing this technique in association with BlueBravo, a group that overlaps with a Russian APT, and Magniber, a recently active ransomware-as-a-service operation.
Atomic Red Team provides two ways to quickly simulate implementations of this technique in all three major operating systems, by either launching a masquerading executable or by creating a process from a masquerading directory. Pivoting from the Technique Details page, I quickly identified this Sigma rule that aligns with the procedure used in the first test, as well as this rule to detect process creation from potential masquerading directories (although this rule focuses on Windows, not MacOS/Linux like the second Atomic test involves).
Mark-of-the-Web Bypass (T1553.005)
Introduced in 2021, this sub-technique, a child of Subvert Trust Controls, has yet to see a high volume of references in threat reporting. However, as adversaries evolve their TTPs, often in response to new countermeasures (in this case, Microsoft’s blocking of Internet-downloaded, Macro-enabled documents starting last February via the Mark-of-the-Web (“MotW”) feature), we observed more reporting that explicitly referenced it. We added three T1553.005 references to our knowledge base last month, mainly callbacks to MotW bypass activity observed earlier in 2022 (for example, The DFIR Report’s new incident response report on an Ursnif banking trojan infection from August).
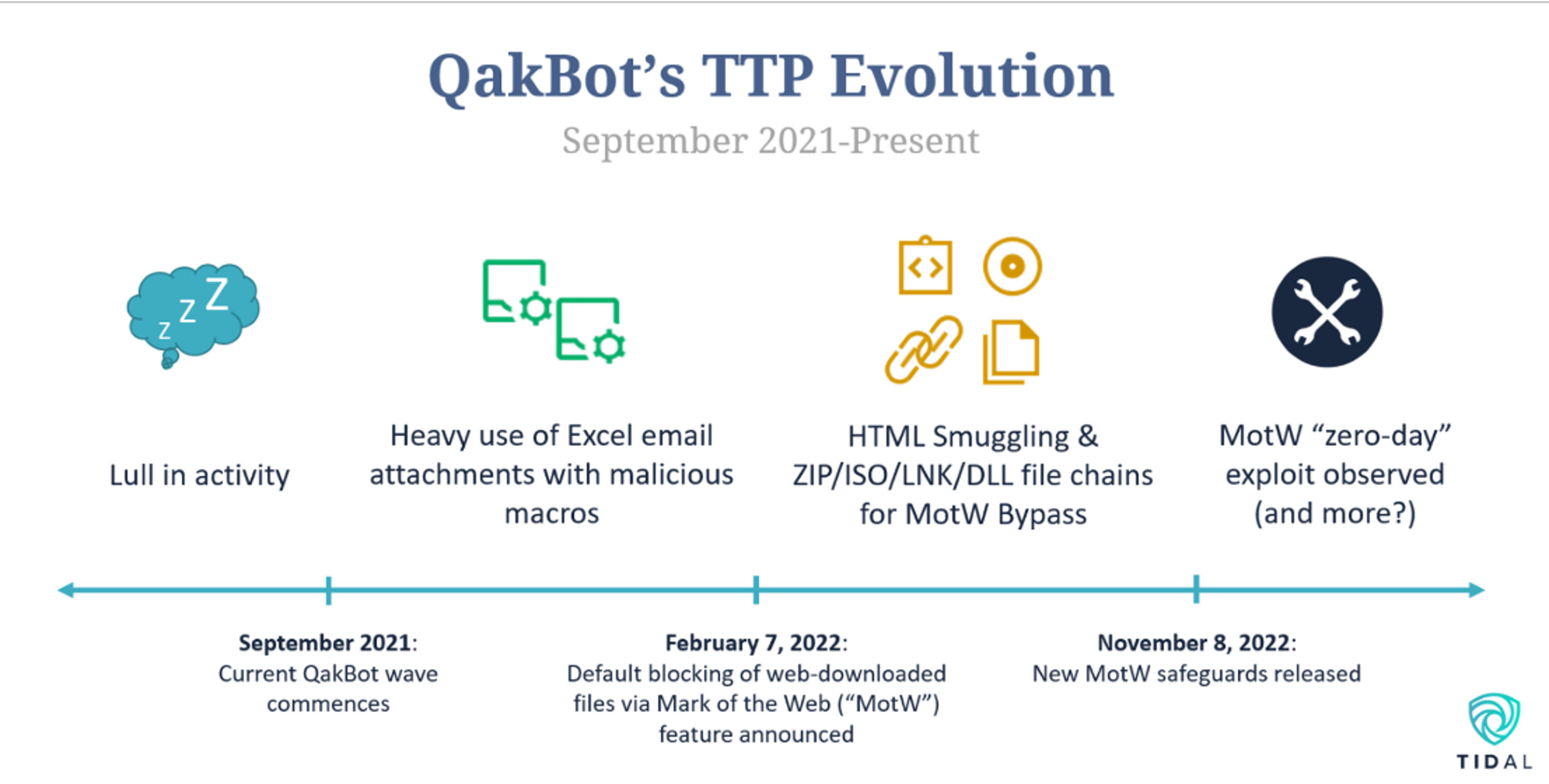
In November, Microsoft extended the MotW security feature to files contained within ISO images, a popular MotW bypass method. Following this development, now could be a good time to validate how MotW defenses, including built-in protections and any supplemental detections, are functioning within your own environment. Public resources to support this effort could include the four Atomic Red Team tests and three Sigma analytics currently mapped to this technique. Micah Babinski also gives a great general detection engineering walkthrough (and rules) around MotW bypass-related infection chains here. Keep in mind that adversaries, including Magniber and QakBot, have been observed using other methods to bypass MotW too, a shift we covered in our QakBot TTP trend analysis last year.
Install Digital Certificate (T1608.003)
Last month gave us a relatively rare sighting of our final spotlight sub-technique, a child of the Stage Capabilities technique. Adversaries use T1608.003 to develop their resources ahead of an attack, specifically by installing SSL/TLS certificates, which enable secure communication between systems, on infrastructure that they have acquired or previously compromised. The reference came from a Mandiant report about its discovery of an operation by Turla, a Russia-based espionage group believed to have connections to the Russian Federal Security Service.
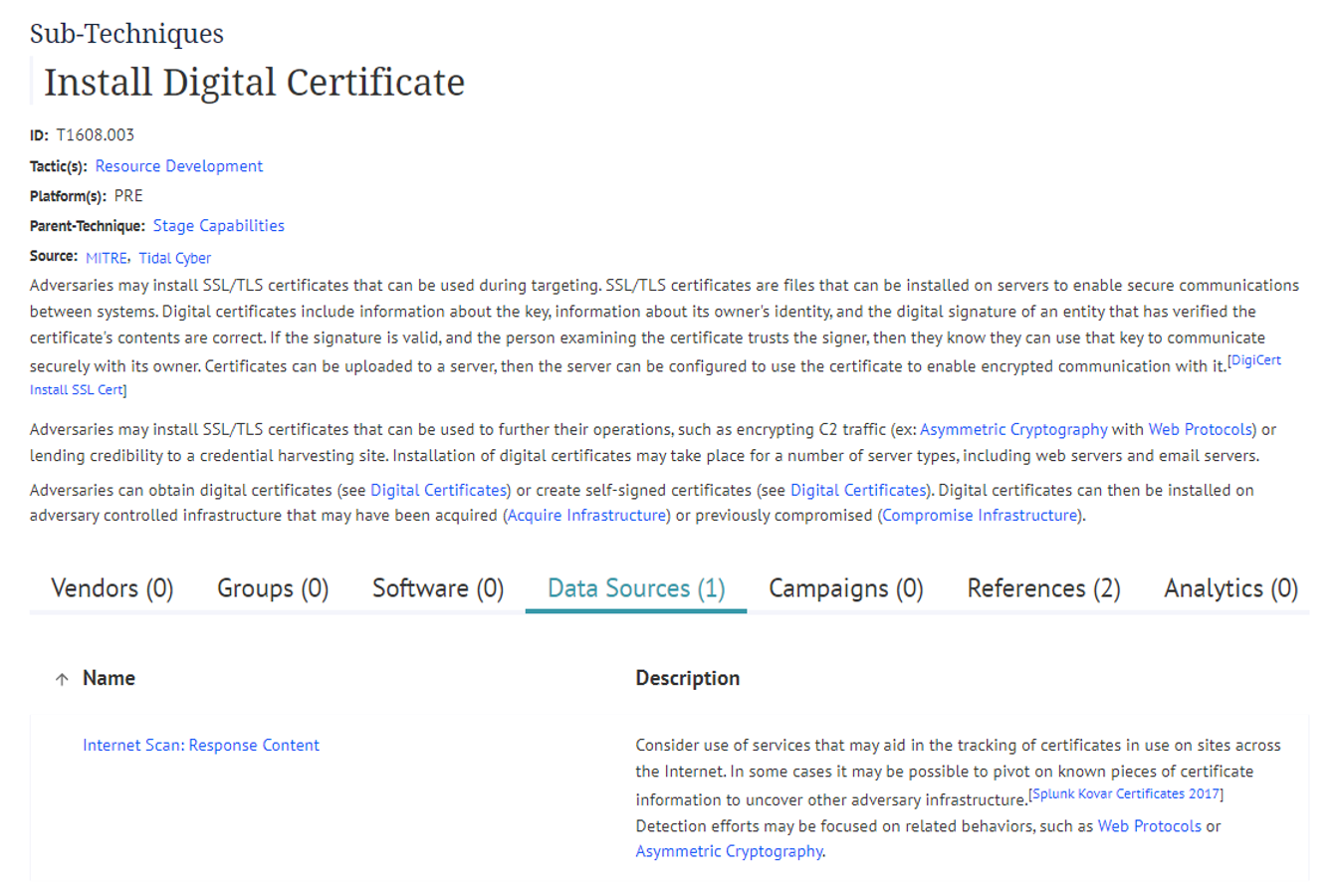
T1608.003’s Technique Details page highlights how relatively few observations exist around this technique currently, as well as supporting defensive resources, a fairly common occurrence for Resource Development and Reconnaissance techniques. However, techniques like these provide a great reminder of the value offered by taking an “in-depth” approach to defense that includes safeguards across the phases of the attack lifecycle. For example, as the ATT&CK Data Sources content for this sub-technique notes, even if direct observation of adversary-installed certificates proves challenging, “Detection efforts may be focused on related behaviors, such as Web Protocols or Asymmetric Cryptography.”
Stay tuned for our next Making Waves TTP analysis next month!


