We are thrilled to share that we have migrated Tidal Cyber’s Community & Enterprise platforms to v16 of MITRE ATT&CK® the day following the new version’s release! Users of ATT&CK know the anxiety that accompanies the release of numerous new Techniques, threats, and defensive content, and many updates & changes to existing content. Tidal Cyber takes many steps to insulate our users from that anxiety and support fast and worry-free migrations with each new ATT&CK release.
Learn more specifics of our process and other ways that Tidal Cyber continually enhances the ATT&CK experience:
Helping Users Navigate ATT&CK Platforms Updates
One of the biggest changes the ATT&CK team made in this release was to restructure platforms. While the majority of the changes were simply name changes, the most impactful change was merging Office 365 and Google Workspace into a single platform. While they had valid reasons for the change, our personal experience from delivering Tidal Cyber is that platforms are a continual place for confusion, especially around capturing nuances between similar, but different platforms.
Given the fact that abstraction isn’t always beneficial, Tidal Cyber has decided to support both the new, abstracted platform, but also continue to allow users to leverage the old platforms. This ensures users can use mappings they already have, and benefit from granularity where needed. This does highlight another change to Tidal Cyber – specifically we have found the abstraction to IaaS does not provide enough granularity for our users who want to assess coverage differences between different IaaS solutions they use. Users want the ability to define coverage of Azure, AWS, and GCP independently. For instance, does the detection apply to AWS, GCP or both? If you are assessing coverage, you need to be able to differentiate between these platforms and their related capabilities. Tidal Cyber will not only support the new abstracted Office platform, but also support a new, more granular IaaS platform.
The good news is that Tidal Cyber has you covered either way. We support the new and the old platforms natively. This flexibility is key for enabling the ATT&CK community to align to how they think about security, once again showing how Tidal Cyber lets users make ATT&CK their own.
Enriched & Extended Threat Intelligence Content
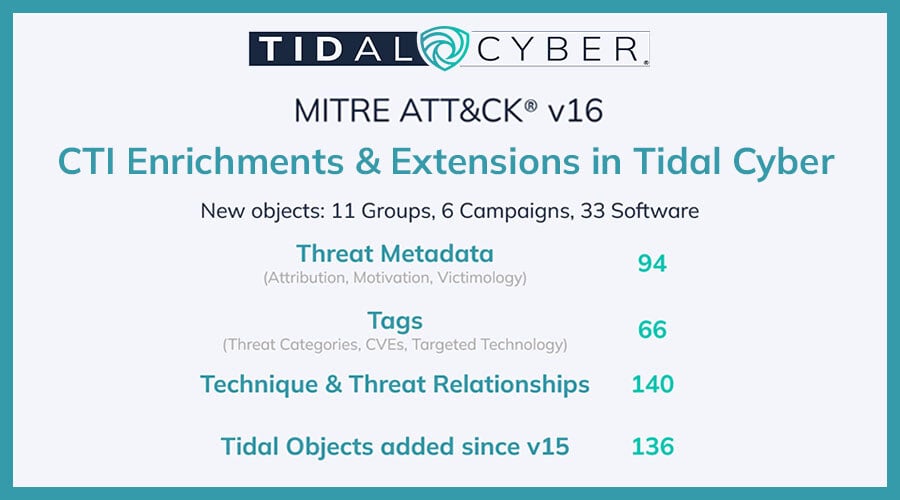
A primary goal of Tidal Cyber’s Adversary Intelligence team is to add threat intelligence content – both new, original content and “extensions” to ATT&CK – to the knowledge base to help users make the most of the platform’s features. We also encourage Enterprise Edition users to enable our “Get-CTI” integrations with many major intelligence providers. For the first time, we enriched and/or extended every new threat object added in the ATT&CK v16 update at release, meaning users immediately had a consistently more-complete view of the constantly evolving landscape within Tidal Cyber the day after v16 became available.
Highlights include the addition of dozens of metadata labels tracking adversary attribution, motivation, and victimology, and Tags that categorize types of adversary tools, vulnerabilities exploited, technologies targeted, and high-confidence sources of information. Our team continually -weekly at minimum- adds threat content, so we’ve also done the heavy lifting to review the several (15) cases where v16 objects overlapped with pre-existing Tidal Cyber Groups, Campaigns, or Software and migrated existing enrichments & extensions to the relevant MITRE objects. Great examples include the Play group, whose Technique Relationships we extended with intelligence from government advisories, and INC Ransom, a group where we added several publicly reported relationships with commonly used ransomware..
We were thrilled to see the addition of several new Techniques that recognize both emerging landscape activity and more established behaviors that were not yet tracked in ATT&CK. In multiple cases where ATT&CK has yet to link any specific threats to new Techniques, we were immediately able to extend the Techniques with relationships to threat objects previously published by Tidal Cyber. In order to rapidly support our Enterprise users leveraging Tidal Cyber Coverage Maps, we also immediately released custom threat weightings for each of the 19 new v16 (Sub-)Techniques (users can always customize weightings to their needs), rolling these updates out alongside our regular periodic weighting updates informed by our continual monitoring & expert analysis around the threat & TTP landscape.