We are excited to announce that the Tidal Cyber Enterprise and Community platforms are now on the newly released Version 15 (v15) of MITRE ATT&CK®! Tidal allows defenders to make the most out of ATT&CK – and the many other threat- and defensive-related resources aligned with it – in pursuit of operationalized Threat-Informed Defense.
Tidal makes it seamless for users to always be on the latest version of ATT&CK, meaning they can access all the latest knowledge base content, including the latest Techniques and Sub-Techniques, threat objects like Groups, Campaigns, and Software, and defensive content like Data Sources and Mitigations. This is complemented by the Tidal-curated content added to the platform every week, ensuring you always have access to the most complete picture of the threat landscape.
Keep reading for key highlights of the v15 release, which you can see within Tidal alongside other recent updates to the platforms.
Exploring the Latest ATT&CK Updates in Tidal
The Threat-Informed Defense community continues to benefit from more content aligned with ATT&CK Techniques & Sub-Techniques, and by bringing much of this into a single platform, Tidal allows users to take full advantage of each new update to ATT&CK. 
Figure 1: The Tidal platforms “connect the dots” in the universe of ATT&CK-aligned content, allowing defenders to optimally leverage various resources, including ATT&CK knowledge base elements at the foundation, but also popular community projects, security vendor product mappings, and third-party threat intelligence.
ATT&CK v15 includes many notable additions and updates, including many that reflect key trends in the landscape. Below are a few highlights, along with links to the Tidal platform for further exploration and pivoting to related resources:
- 1 new Technique and 11 new Sub-Techniques: Additions underscore adversaries’ growing adoption of artificial intelligence, focus on compromising less-protected edge devices, and constant attempts to further conceal their activities.
- 29 new Adversary Software: These include multiple prominent threats used to gain initial footholds into victim networks. This access is often resold by criminal actors, a trend we emphasized throughout our research over the past year (see for example our Q2 threat landscape briefing and our presentation at Sleuthcon in May!).
- 7 new Groups: Like many ATT&CK releases, v15 includes new espionage actors, but it also saw the addition of ransomware and other financially motivated groups. Tidal’s team monitors closely for emerging threats, and in many cases had already released objects around content published in v15, which are now integrated with the ATT&CK versions (for example, Enterprise users received content related to Akira ransomware last August, which we also shared with Community users in early April as Akira victim tallies continued to rise).
- 5 new Campaigns: Including intrusions like Cutting Edge that reflect the ongoing trend of state-sponsored vulnerability exploitation, especially attacks targeting network devices.
- Updated formatting to defensive analytics is now provided in many ATT&CK Data Sources. See also the Tidal Analytics library for a robust collection of Sigma analytics (a vendor-agnostic detection logic format) derived from multiple community sources.
Enriching & Extending ATT&CK CTI Content
Tidal Cyber’s Adversary Intelligence Team continuously enriches and extends ATT&CK cyber threat intelligence (CTI)-related objects, giving users a more complete picture of the adversarial behavior and threat landscape. Each week, we author original threat objects that look and feel just like those found in ATT&CK, “extend” ATT&CK objects by adding new Technique Relationships and apply numerous structured metadata and Tags to ATT&CK and Tidal-authored objects.1
 Figure 2: Summary of v15 objects enriched & extended by Tidal’s Adversary Intelligence Team.
Figure 2: Summary of v15 objects enriched & extended by Tidal’s Adversary Intelligence Team.
Figure 2 summarizes Tidal content extensions to select ATT&CK v15 objects, and Figure 3 shows one of the many rich examples from our free Community Edition.
 Figure 3: The “Akira” Group as seen in the Tidal Cyber platforms (access it in Community Edition here). This object is authored by the MITRE ATT&CK team but enriched by Tidal with helpful structured metadata and Tags.
Figure 3: The “Akira” Group as seen in the Tidal Cyber platforms (access it in Community Edition here). This object is authored by the MITRE ATT&CK team but enriched by Tidal with helpful structured metadata and Tags.
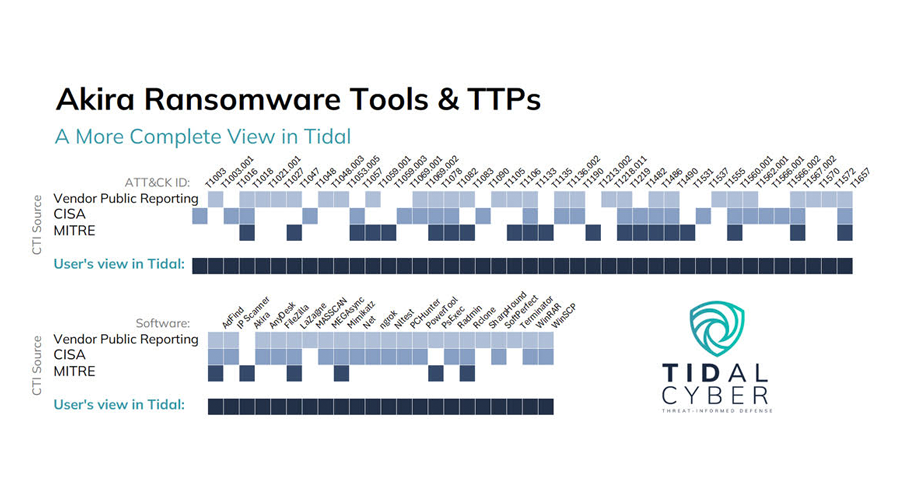
Figure 4 below highlights a timely example of how using Tidal gives defenders a more complete and timelier picture of the behaviors used by key cyber adversaries. By routinely (each week at minimum) updating our knowledge base with timely intelligence around current threats from a large number and variety of trusted sources, Tidal users can be sure they are making the most out of both ATT&CK and the increasing number of third-party data sources that align with it. Be sure to check the Community Edition homepage each week for spotlights on the latest additions.
 Figure 4: Through regular, timely intelligence updates derived from various trusted sources, the Tidal Cyber platforms provide a more complete picture of the adversary threat landscape.
Figure 4: Through regular, timely intelligence updates derived from various trusted sources, the Tidal Cyber platforms provide a more complete picture of the adversary threat landscape.
While Community Edition users gain access to all the intelligence, mappings, and other data above, Enterprise Edition users can prioritize and apply it to their defensive stacks to make more quickly informed decisions about their security coverage. Read more about Tidal Cyber Enterprise Edition or sign up for Community Edition.
1 These metadata and Tags are especially helpful for Threat Profiling purposes. Read more about Tidal’s structured approach to threat profiling in our free, 60-page e-book here.