Recent reporting highlighted new techniques for a prominent group that already possessed a deep set of capabilities. As the pace of adversary TTP evolution increases, organizations must stay vigilant and regularly reassess their defenses against the latest TTPs used by relevant threats. This holds true even amid reports of threat group disruptions, as many groups continue to demonstrate resilience in the face of law enforcement operations and other pressures.
Scattered Spider’s Shift to SaaS
Scattered Spider is one of the cyber landscape’s most prominent current threats, a financially motivated group responsible for multiple high-profile attacks on prominent brands over the past two years. On June 13, Mandiant researchers published a blog that detailed Scattered Spider actors’ targeting of software-as-a-service (“SaaS”) environments for data theft since August 2023, marking a shift from earlier operations that focused on credential harvesting, SIM swapping, and ransomware-based extortion.
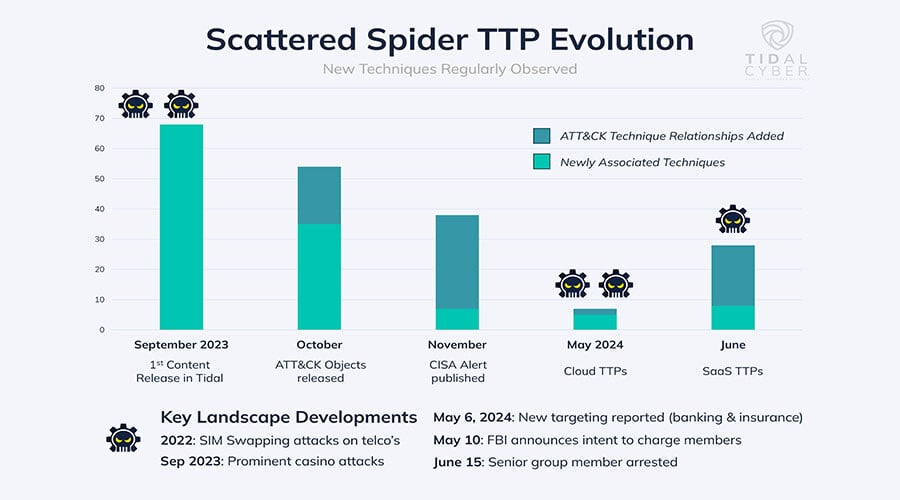
Like it does every week, Tidal Cyber’s Adversary Intelligence Team reviewed the blog (and other recent Scattered Spider reporting) for references to MITRE ATT&CK® tactics, techniques, and procedures (TTPs), which allow defenders to more readily and consistently consider relevant defenses. As Figure 1 shows, we’ve identified a very large number of Scattered Spider ATT&CK TTPs since starting to closely track this group, with new reports usually highlighting both previously and newly observed techniques, and the new blog was no different.

Figure 1: Visual summary of Scattered Spider’s TTP evolution. Even as the list of known behaviors grew, subsequent reporting typically revealed net-new TTPs.
We published a new Campaign that summarizes Scattered Spider’s targeting of SaaS environments, which highlights 26 ATT&CK Techniques, most of which represent previously known methods for initial access, internal reconnaissance, and privilege escalation. However, eight Techniques were associated with Scattered Spider for the first time. Notable examples include its efforts to achieve persistent SaaS access via SAML Token forgery (T1606.002), its methods of tampering with security tools & logging and even leveraging security tools for command execution (T1562.001, T1070.001, & T1518.001), and use of system firmware modifications to maintain stealthy footholds (T1542.001).
A Case Study in TTP Evolution
Scattered Spider represents one of the clearest examples yet of a landscape trend we have spotlighted for some time: the increasing pace of adversary TTP evolution. As adversaries increasingly adapt and expand their capabilities, organizations must also position themselves to continually reinforce, validate, and optimize their defenses in line with both well-known but especially recently observed behaviors associated with the threats they care about.
Figure 1 highlights how, even as the list of known Scattered Spider behaviors continued to grow, new reporting would typically reveal additional TTPs used by the group. Behaviors are (rightly) traditionally perceived as less “volatile” than other adversary indicators like elements of their infrastructure (IOCs) or exploited vulnerabilities (CVEs), meaning they are expected to change less regularly. However, as threat actors pursue new targets (often motivated by lucrative financial gain) or adjust to new security measures, they are now even changing their TTPs with alarming regularity.
As Figure 1 shows, new Scattered Spider TTPs aren’t necessarily identified every day or week (like new command & control IP addresses or phishing domains), but we are witnessing behavioral evolution on a quarterly to monthly basis. Even if your security team performed the often resource-intensive process of identifying, creating, deploying, validating, and tuning new security measures against Scattered Spider’s known behaviors last quarter, TTP evolution may necessitate that it repeats the cycle but now focused on the group’s latest capabilities.
Adversary Resilience
Readers might wonder why a new Scattered Spider TTP analysis is useful days after authorities arrested a senior member of the group (the latest in an increasingly regular cadence of law enforcement operations against prominent threats). Considerable evidence indicates groups like Scattered Spider are highly resilient, and we encourage continued vigilance against the group’s TTPs in the near-term, whether they are used by other group members or entirely distinct actors.
True to its name, dispersed operations are a hallmark of Scattered Spider, meaning an arrest of even a senior member likely will not halt its activities outright (authorities describe it as a “very large, expansive, disbursed group” comprised of hundreds of members but still employing consistent techniques). Even as U.S. officials announced they were building charges against Scattered Spider members, the group continued to expand its range of targets, demonstrating persistent intent amid law enforcement pressure.
Even if future operations further disrupt Scattered Spider, it is unlikely that they would “dismantle” the group entirely. Cases abound where adversary groups splintered and reconstituted in the face of law enforcement operations and other environmental pressures, including changing security measures, geopolitical factors, and even internal turmoil: prominent examples include many ransomware groups and other criminal operations. TTP reuse (by actors not affiliated with Scattered Spider at all) presents a final, notable concern, especially considering how successful some of the group’s techniques appear to have been (and amplified by how widely TTPs were shared among the group’s many members).
Defenses
Mapping adversary capabilities to ATT&CK streamlines defenders’ ability to pivot to resources across the range of defensive capability types, and Tidal’s Enterprise Edition makes it easy to continually reassess defensive confidence even as the pace of adversary TTP evolution increases.
To demonstrate, we aligned our recently updated “Scattered Spider Ecosystem” curated Threat Profile (containing the key tools & campaigns related to the group and all the Techniques associated with them) against the full range of Mitigations published in ATT&CK, to generate a rank-ordered list of which Mitigations provide the most defensive value against this large volume of tools & TTPs. User- & identity-focused measures topped the list, including Privileged Account Management (aligning with 54 Scattered Spider techniques), as well as strong Password Policies, User Training, and Multi-Factor Authentication, which can all mitigate more than 25 techniques.
It is worth noting that these rankings changed considerably when comparing Mitigations against early versus recent campaigns, with measures like configuration policies emphasized more in the latter cases. Enterprise Edition allows users to model their entire Defensive Stack, across all capability types (beyond just Mitigations), giving insight into high-priority protection, detection, logging, response, and testing opportunities for recent Scattered Spider behaviors as well.
Want to learn more about mapping these types of adversary capabilities across your defensive capabilities? Reach out to us.