Register here for our upcoming Surf Report webcast, where we’ll summarize top TTPs and defensive takeaways across Q2 2023!
The Making Waves series takes a data-driven approach to spotlighting MITRE ATT&CK® techniques that are “trending” in public reporting (or alternatively, techniques that tend to be cited infrequently). The June edition takes a different approach than other recent entries. This month, we spotlight techniques that were newly added to the ATT&CK knowledge base as part of its v13 update, released in late April. We anticipate that the threat reports highlighted below contain what are likely the first public (explicit) references to these techniques.
References to these new ATT&CK techniques just weeks after their release further underscores the adoption of MITRE ATT&CK in the threat research community. As we’ve highlighted previously (and demonstrate through this monthly blog series), the increased volume of ATT&CK-mapped intelligence provides valuable opportunities for measuring changes in technique reference volumes over time, an especially important task as adversaries continue to modify and evolve their TTPs with increasing regularity.
Tidal’s freely available Community Edition supports v13 of ATT&CK, meaning users can be sure their threat informed defense research and analysis aligns with the latest version of the knowledge base.
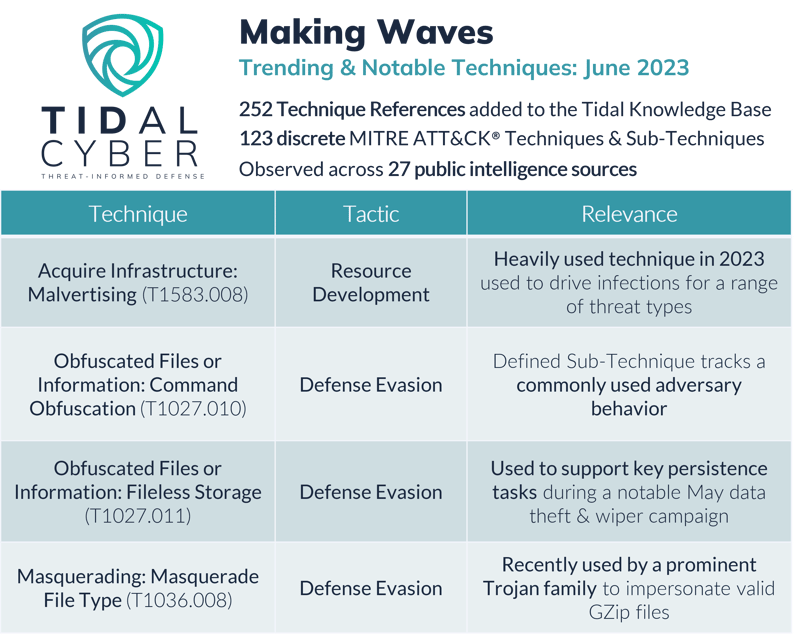
In June, our Adversary Intelligence team added 252 technique references to the Tidal knowledge base, which were observed across 27 public sources. In total, these references covered 123 discrete techniques, or 20% of the 607 techniques & sub-techniques currently included in the ATT&CK knowledge base. In recent weeks, we identified references to four techniques newly added to ATT&CK in its v13 update:
Acquire Infrastructure: Malvertising (T1583.008)
Malvertising represents one of several ways that adversaries Acquire Infrastructure in order to develop their resources for launching cyber attacks. Malvertising refers to the purchase of legitimate online advertisements to distribute malware. While malvertising is by no means a novel technique, its inclusion in ATT&CK in April is timely, since a range of adversaries have heavily relied on it throughout 2023 to drive victim traffic to compromised infrastructure for initial access purposes.
T1538.008 references since Malvertising’s inclusion in ATT&CK in April include the Trend Micro incident response team’s recent discovery of a campaign that used malvertising to drive phishing attacks for initial access and backdoor installation (in one instance leading to BlackCat ransomware deployment) and an earlier set of attacks linked to backdoor- and ransomware-focused actors. Tidal previously highlighted malvertising’s prominence as an infostealer delivery mechanism in 2023, and the technique is also a prominent infection vector for initial access threats that are used to deliver a range of other, often more-impactful malware.
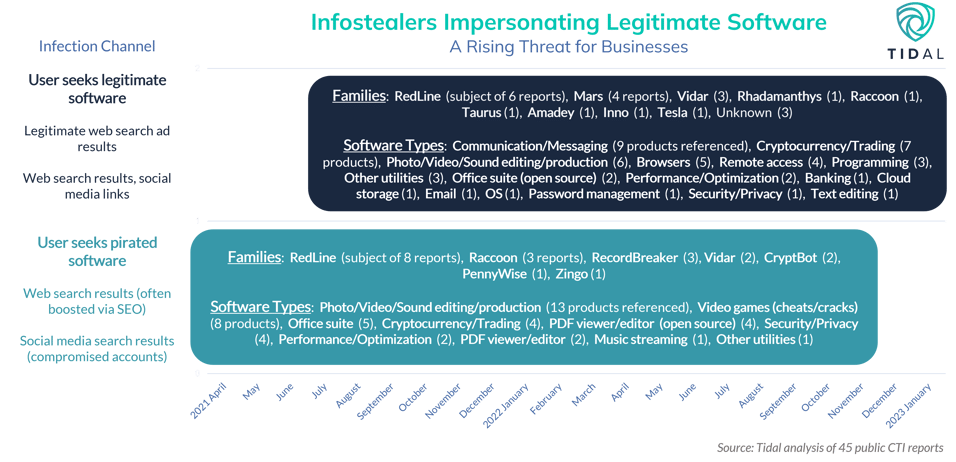
An infographic from Tidal’s infostealer threat landscape series highlights the recent threat posed by Malvertising as an initial infection vector for a range of prominent infostealers.
Obfuscated Files or Information: Command Obfuscation (T1027.010)
This technique represents one of the myriad ways that adversaries attempt to obfuscate files or informationassociated with their activities, in order to evade defenses (there are now 11 discrete Sub-Techniques under this parent Technique, including another new one discussed further below). Specifically, it refers to ways adversaries attempt to make strings and/or patterns within commands and/or scripts more difficult for defenders to recognize, both through commands executed by delivered payloads, as well as interactively via a Command and Scripting Interpreter.
As many readers will likely know, this activity is very common, but the introduction of a defined Sub-Technique for it provides a way for practitioners to consistently refer back to its observation. The ATT&CK knowledge base already associates 25 Groups, 27 Software, and five Campaigns with this new Sub-Technique. In May, Tidal observed a reference to T1027.010 in the Securonix Threat Labs Security Advisory on a phishing campaign that used “meme-filled code” and various other obfuscation methods to ultimately deliver payloads of the XWorm remote access Trojan (“RAT”). Many blocks of PowerShell code in the initial payload featured heavy command obfuscation via string substitution and hex formatting, many examples of which can be seen throughout the source report. Of note, we observed another explicit T1027.010 reference more recently in the latest The DFIR Report investigation, where the FlawedGrace RAT used obfuscated PowerShell commands to create scheduled tasks for malware execution purposes.
Obfuscated Files or Information: Fileless Storage (T1027.011)
This is another adversary obfuscation method that refers broadly to storing data in any format other than a file, again for evasion purposes. Like for pre-existing fileless/in-memory ATT&CK techniques like Reflective Code Loading or Process Injection, antivirus or other endpoint security technologies may not detect adversarial activity involving fileless storage if they only access on-disk file formats. The Fileless Storage Sub-Technique can refer to storage of payloads or shellcode in non-file formats, as well as to storage of staged victim data.
Two Groups, 25 Software, and one Campaign already map to this Sub-Technique in the ATT&CK knowledge base, underscoring its relatively common usage. The explicit T1027.011 reference we identified in public reporting in May involved a common implementation of the Fileless Storage Sub-Technique: data storage in the Windows Registry. In this example, security researcher cocomelonc provided a walkthrough of multiple C++ code examples for storing binary data in the Windows Registry. The more recent The DFIR Report investigation mentioned above featured a second reference to this Sub-Technique, which also involved data storage in the Windows Registry. In this case, FlawedGrace RAT stored elements of scheduled task-related PowerShell code as Windows Registry Key values.
Masquerading: Masquerade File Type (T1036.008)
This Sub-Technique represents one of several ways adversaries seek to mimic legitimate files in order to evade defenses. In this case, it refers to methods of changing a payload’s formatting, which could include changes to the file’s signature, extension, and/or its contents. Adversaries will often disguise malicious files with extensions typically treated as benign (such as .txt text files or image files), which can be effective if a user does not closely inspect other file metadata.
Three Software and two Campaigns mapped to this Sub-Technique at ATT&CK v13’s release in April. Shortly after, Elastic Security Labs researchers reported on recent IcedID samples they analyzed, which also used this Sub-Technique. In these instances, IcedID payloads were typically packed into custom file formats, but they masqueraded as legitimate GZip files by encapsulating real data with valid GZip headers and footers.


