September 25, 2024 Update:
- Added two recently identified backdoor malware, Spearal & Veaty, linked to the OilRig espionage group
- Added numerous Exploited Vulnerabilities enrichments for several of the actor groups highlighted below
- Added visual summaries of the overall targeting patterns & adversary software types associated with the key groups highlighted in this blog
Multiple types of organizations around the world are currently facing heightened threats from Iran-aligned cyber actors. Researchers continue to report significant increases in Iran-aligned threat activity well after the start of the Israel-Hamas War in October 2023. In recent weeks alone, Iran-backed groups deployed new malware for long-term intelligence collection, compromised U.S. presidential campaign systems, and even collaborated to ransom entities in critical U.S. and foreign industries.
Whether you are a defender who wants to quickly assess defenses against all current major threats or an analyst looking to pinpoint certain groups with relevant motivations or targeting patterns, this resource aims to help by highlighting numerous links to recent adversary, tool, & TTP intelligence from across the Tidal Cyber knowledge base.
How to Operationalize This Intelligence: Tidal Cyber is specifically designed to operationalize adversary behavioral intelligence. The free Community Edition lets defenders easily pivot from or compare adversary TTPs to elements of their defensive stack (60-second tutorial). The Enterprise Edition platform supercharges this workflow with easy-to-maintain collections of relevant threats, fully featured Defensive Stacks, and continually updated Coverage Maps.
Supporting Resources
- Election Threats & Defenses Report: An original, data-driven study on cyber threats to global elections in 2024, highlighting various attacks and threats associated with Iran-linked actors
- The Ultimate Guide to Cyber Threat Profiling: A detailed guide to identifying & prioritizing relevant cyber threats. Iran-aligned actors are known to target a wide variety of organizations, meaning at least some of the actors featured here usually appear in a cybersecurity team’s threat profile.
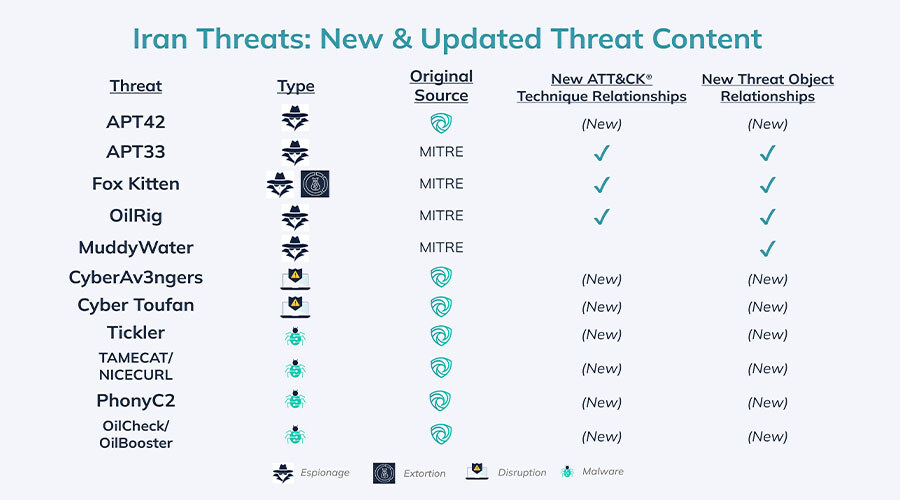
Key Cyber Threats

Figure 1: All objects highlighted here are authored by the Tidal Cyber Adversary Intelligence team or are MITRE ATT&CK® objects that feature original ATT&CK Technique and/or related object “extensions” based on recent intelligence. Most objects also feature Tidal-curated metadata and/or Tag enrichments.
Prominent Groups
- APT33 (aka Peach Sandstorm, et al.): Espionage group believed to operate on behalf of the Iranian Islamic Revolutionary Guard Corps (IRGC, a U.S.-designated terrorist unit). Leverages extensive pre-attack reconnaissance, password spraying, and (recently) cloud-based attacks.
- APT42: Espionage group believed to operate on behalf of the IRGC Intelligence Organization (IRGC-IO). Known for invasive surveillance activity, including a recent hack on a U.S. presidential campaign.
- Fox Kitten (aka Pioneer Kitten, et al.): Espionage group associated with the Iranian government that also collaborates to carry out ransomware-focused extortion attacks. Subject of a recent joint Cybersecurity Advisory spotlighting recent attacks on critical U.S. and foreign organizations.
- MuddyWater: Cyberespionage group associated with Iran's Ministry of Intelligence and Security. Targets a wide range of sectors and geographies for intelligence gathering.
- OilRig: Suspected Iran-based espionage group. It also targets a wide range of victims, including via supply chain attacks.
- Magic Hound (aka APT35, Charming Kitten, Phosphorus, et al.) Also likely operating on behalf of the IRGC. Known for persistent, resource-intensive espionage operations & election interference activity.
- CyberAv3ngers: Likely affiliated with the IRGC. CyberAv3ngers reportedly compromised and defaced U.S. water utility systems in November 2023 as part of a broader campaign targeting systems that used technology associated with Israeli manufacturers.
- Cyber Toufan: Researchers label this an "Iranian-affiliated", "hacktivist proxy" group. Mainly targets organizations based in or perceived to be aligned with Israel. Focuses on destructive attacks but also often leaks victim data allegedly exfiltrated during intrusions.
Several other relevant groups can be found using the “Suspected Attribution” filter on the Groups List page: https://app.tidalcyber.com/groups

Figure 2: A summary of the targeting patterns and other Tidal Cyber knowledge base metadata associated with the key Iran-aligned threat groups highlighted in this blog.
Notable Software
- Tickler: Newly discovered multi-stage backdoor deployed by Peach Sandstorm (APT33)
- TAMECAT & NICECURL: Custom backdoors developed and used by APT42, usually delivered via spearphishing
- PhonyC2: Command & control framework attributed to MuddyWater, deployed since at least 2021, and regularly updated since that time
- IMAPLoader: A .NET downloader developed by Yellow Liderc that uses email-based channels for command & control
- Mimikatz: While this open-source credential stealing tool is used by a wide variety of actors, it is worth highlighting that it has been linked to at least seven of the Iran-aligned groups tracked in our knowledge base (more than any other individual software)
Many other relevant Tools & Malware can be surfaced by pivoting to the Software tab on Group (above) or Campaign pages (below).

Figure 3: A summary of the targeting patterns and other Tidal Cyber knowledge base metadata associated with the key Iran-aligned threat groups highlighted in this blog.
Campaigns
- IRGC Data Extortion Operations: Actors targeted victims in a wide range of U.S. critical infrastructure sectors, typically exploiting vulnerabilities for initial access
- Iranian APT Credential Harvesting & Cryptomining Activity: Actors achieved initial access by exploiting the Log4Shell vulnerability, installed XMRig cryptomining software, and executed Mimikatz to harvest credentials
- Iranian APT Targeting U.S. Voter Data: Unspecified actors targeted U.S. state websites with the goal of obtaining voter registration data using directory traversal, SQL injection, and web shell upload attacks. Officials assessed the same actor then carried out mass dissemination of intimidation emails to U.S. citizens and an election-related disinformation campaign.
Defensive Takeaways
An ATT&CK matrix featuring the associated TTPs for many of the threats highlighted above can be found in our Community Edition here.

Figure 4: Tidal-curated Threat Profile available to Enterprise Edition users.
Enterprise Edition users receive this content as a more robust threat profile, which features additional objects and updates curated by our Adversary Intelligence team. Adding this threat profile to a Tidal Cyber Coverage Map and using the data-driven Tidal Recommendation engine revealed that the following MITRE ATT&CK Mitigations contribute most to improving defensive confidence against the Iran-aligned threats highlighted in this resource:
- Privileged & user account management (M0926, M1018)
- Strong password policies & multi-factor authentication (M0927, M1032)
- System/software/configuration audits (M1047)
- User training (M0917)
- Remove/deny software access (M1042)
- Active Directory configuration (M0915)
The “Prominent Iran-Aligned Threats” Threat Profile can be paired with Defensive Stacks that reflect users’ actual security stacks to generate Confidence Scores, coverage metrics, and Recommendations tailored to their actual operating environments.

Figure 5: A Tidal Coverage Map consisting of the Iran Threats Threat Profile and a representative Defensive Stack.
Again, we are continually updating Community Edition and Enterprise Edition for our users and customers. You can sign up for Community Edition with a few clicks or reach out to us to learn more about Enterprise Edition.