On August 24, Microsoft released details about a newly defined, China-based espionage group known as Flax Typhoon, outlining numerous techniques observed during recent Flax Typhoon intrusions. Assuming a security team deemed this a relevant threat, which techniques should be prioritized for further inspection? Next steps can be time- & resource-intensive – teams often look to: determine which security tools address a particular technique, develop & deploy new countermeasures, verify logging, and validate that defenses work as expected. This blog highlights common prioritization factors, then demonstrates how community resources can be applied to speed up detection development & validation around Flax Typhoon persistence methods (and, importantly, plausible variations on observed behaviors).
Flax Typhoon is a nation-state espionage actor based in China that has targeted government, education, manufacturing, & IT organizations in Taiwan and multiple other regions. Microsoft warned that Flax Typhoon's techniques, which lean on legitimate, often built-in tools & utilities, could be used in attacks on victims in other locations, underscoring its wider relevance. Like growing numbers of threat reports, Flax Typhoon’s was helpfully mapped to MITRE ATT&CK®, which quickens intelligence processing & operationalization. We added a collection of the referenced techniques to our free Community Edition hours after the report’s publication. (Enterprise users received Flax Typhoon intelligence as new Group & Software objects, which can be used more flexibly. A Tidal-authored Group object for Volt Typhoon, another new China-attributed espionage group, can be found in Community Edition here.)
We tallied 60 techniques associated with Flax Typhoon and its toolset, including built-in Windows utilities like Reg & certutil and open-source & custom software like Mimikatz and China Chopper. That’s likely too many for most security teams to investigate at once. Common prioritization approaches include techniques that increase an attack’s scope or ones that are central to an overall attack chain. Many practical factors also exist, including whether relevant coverage already exists, whether intelligence is granular enough to inform detection development, and the level of effort required to create, deploy, & validate those detections. Fortunately, granular, command-line-level details were provided for several Flax Typhoon behaviors, and in at least two cases, community repositories contain resources to support detection & simulation of those precise behaviors (note: the source report outlines a number of other detection & mitigation opportunities too).
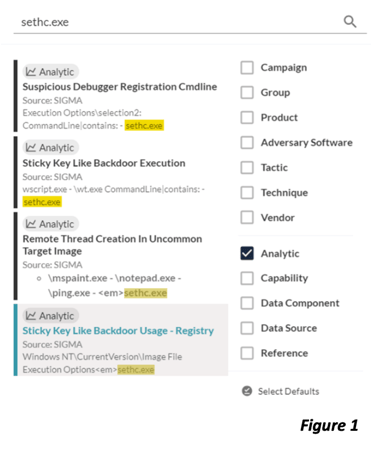 Flax Typhoon’s abuse of Windows accessibility features (T1546.008), where the actors alter the behavior of the Sticky Keys executable so the Task Manager can be launched even if a victim is not signed-in, grants the actor wide command execution privileges and persistence abilities (a stark reminder that well-known techniques continue to be recycled even by nation-state-level adversaries). Community Edition’s recently updated Search functionality allows users to immediately surface detection analytics and vendor capabilities that could be relevant to adversary technique implementations, based on granular evidence such as components of command-line activity. The Search results in Figure 1 contain two analytics from the open-source SigmaHQ repository that directly match the T1546.008 implementation used by Flax Typhoon (the logic is nearly identical but each rule targets a different log source). Rules aggregated in the Community Edition Analytics library provide detection logic that can be translated into specific tools’ query languages to hunt for or alert on myriad adversary behaviors.
Flax Typhoon’s abuse of Windows accessibility features (T1546.008), where the actors alter the behavior of the Sticky Keys executable so the Task Manager can be launched even if a victim is not signed-in, grants the actor wide command execution privileges and persistence abilities (a stark reminder that well-known techniques continue to be recycled even by nation-state-level adversaries). Community Edition’s recently updated Search functionality allows users to immediately surface detection analytics and vendor capabilities that could be relevant to adversary technique implementations, based on granular evidence such as components of command-line activity. The Search results in Figure 1 contain two analytics from the open-source SigmaHQ repository that directly match the T1546.008 implementation used by Flax Typhoon (the logic is nearly identical but each rule targets a different log source). Rules aggregated in the Community Edition Analytics library provide detection logic that can be translated into specific tools’ query languages to hunt for or alert on myriad adversary behaviors.
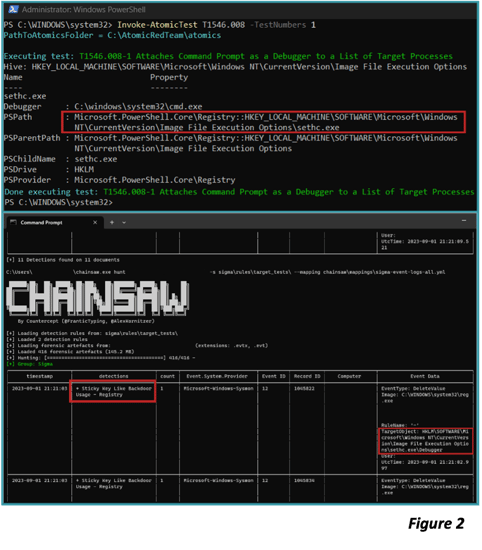
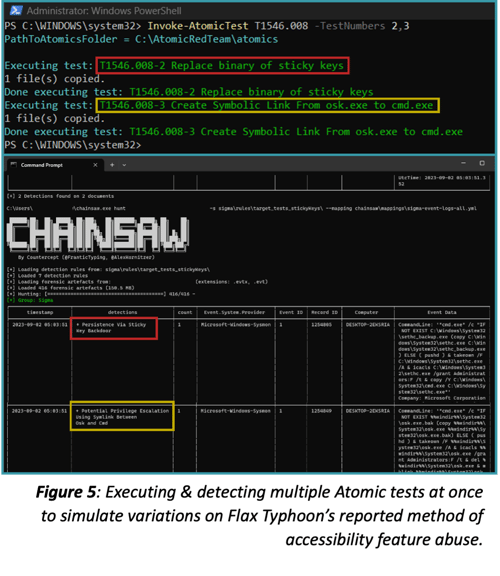
Typos, translation issues, and insufficient logging can cause detections to not trigger as expected, so validation will further increase confidence in deployed defenses. Fortunately, another capability listed in the Product Registry enables simulation of this exact technique implementation: an offensive security unit test from the open-source Atomic Red Team project from Red Canary. Figure 2 shows an immediate detection validation feedback loop (in essence, a miniature Purple Team exercise), fueled entirely by community resources. The author used the Invoke-AtomicRedTeam PowerShell framework to execute the above adversary simulation and the public-source Chainsaw tool to run the target Sigma rule against the machine’s Sysmon logs, which were configured according to Olaf Hartong’s Sysmon-Modular config.
Relevant defensive resources are similarly available for Flax Typhoon’s method of using Remote Desktop Protocol (RDP). The actors change a registry key to disable network-level authentication (NLA) for RDP, allowing them to make the accessibility feature changes described earlier. Searching in Community Edition for the UserAuthentication command-line detail (from the Flax Typhoon report) surfaced this analytic, which targets the precise behavior used by this group. An equivalent Atomic test did not yet exist for this Procedure, but we used the transparent details offered in the Sigma rule and inspiration from the examples above to quickly create a new one and contribute it back for others to use. Figure 3 highlights the key components of the Flax Typhoon Procedures as they appear in respective resources.
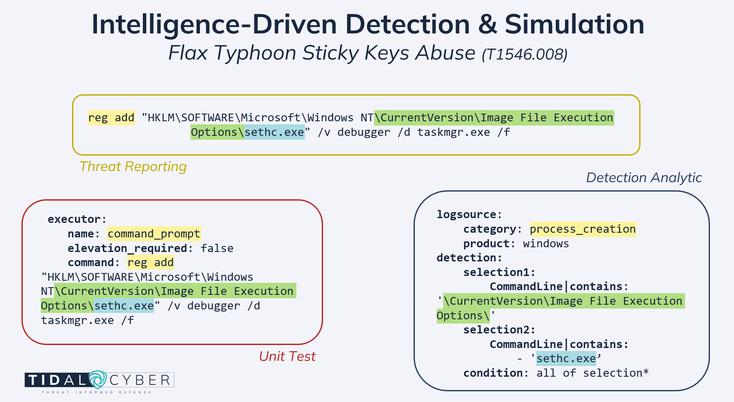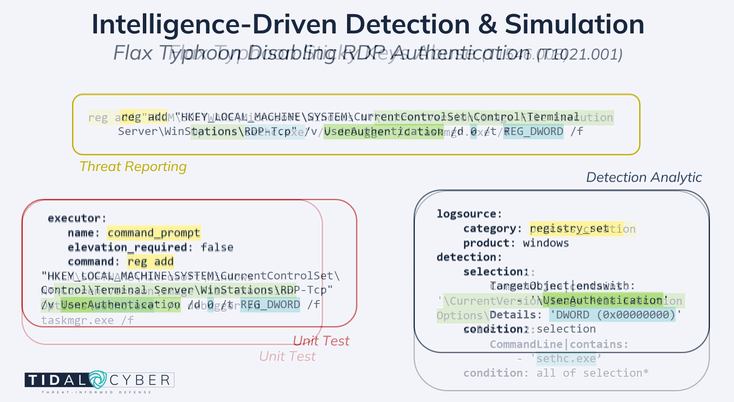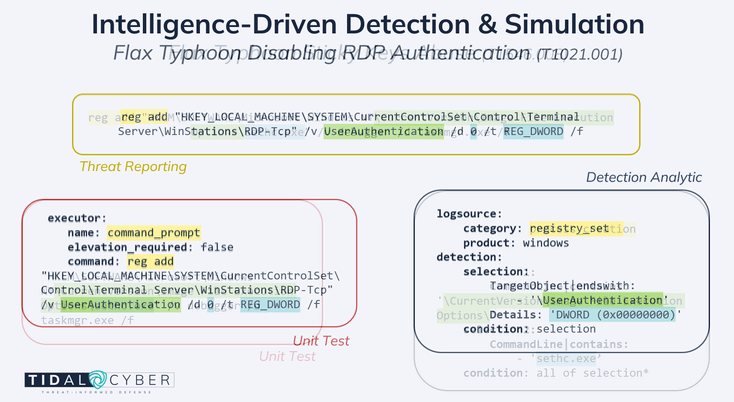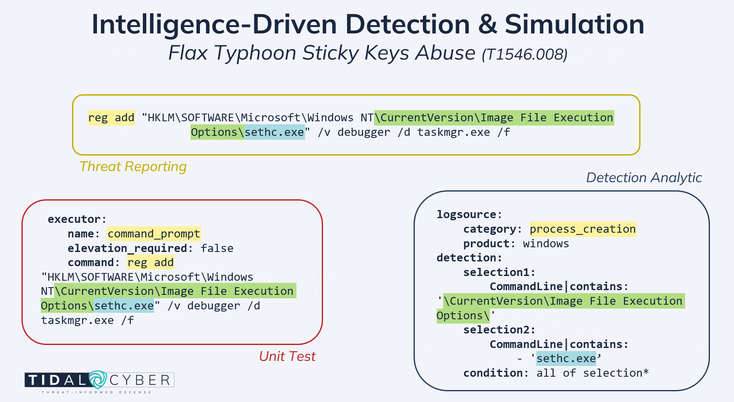
Figure 3
Outside the Box: Detection Validation for Behavioral Variations
As more organizations look to fine-tune their defenses in line with the threats most relevant to them, it is positive that so many resources exist to enable precise detection & simulation of recently reported or observed adversary behavior. However, it is very plausible that a capable group like Flax Typhoon will adjust its attack methods now that they have been widely publicized. As adversaries increasingly evolve their Tactics, Techniques, & Procedures (TTPs), defenders should seek to keep pace in accounting for plausible variations on relevant threats’ behaviors. Fortunately, the same resources highlighted above can help defenders “think outside the box” and readily simulate (and detect) variations on behaviors that would help adversaries achieve the same goals. Technique-level pivoting in Community Edition is a powerful way to approach this task.
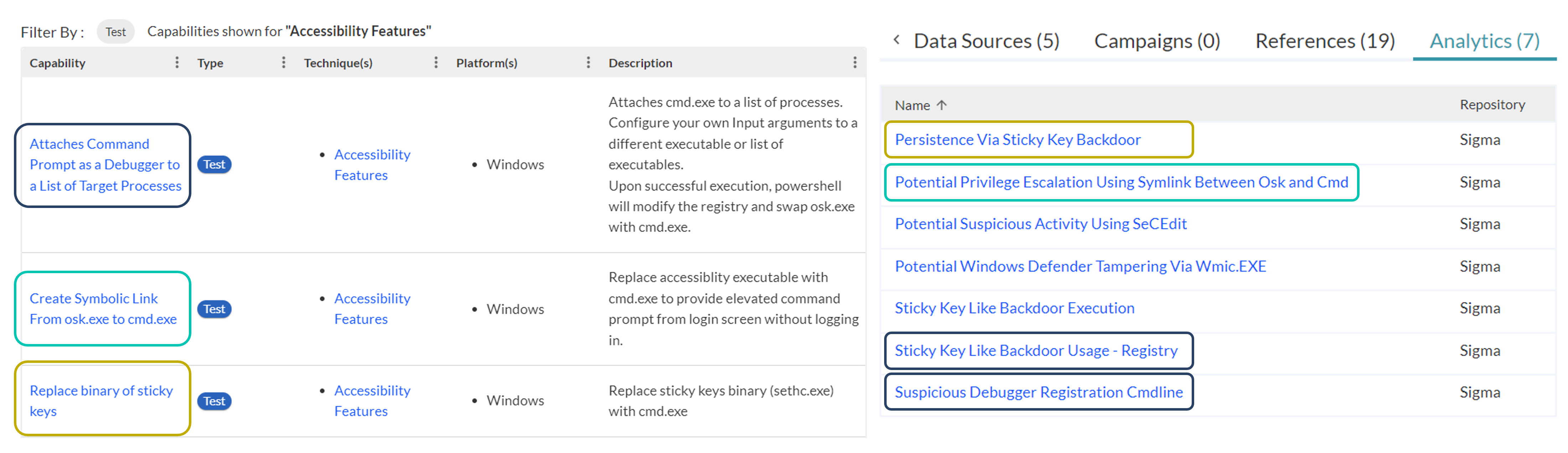
Figure 4: The Accessibility Features Technique Details page contains links to multiple relevant Atomic Red Team resources, as well as Sigma analytics containing directly aligned detection logic.
Since the threat intelligence, defensive, & offensive security resources in Community Edition are all organized around mapped ATT&CK Techniques (and Sub-Techniques), defenders can intuitively pivot from any one of these elements to the others, saving considerable time & effort. For example, navigating to the Technique Details page for the Accessibility Features (T1546.008) technique discussed earlier (see Figure 4) reveals not only the relevant threat information from ATT&CK that defenders are accustomed to seeing, but also numerous defensive & offensive capabilities from partners in the Tidal Product Registry, which also align with this technique. These include commercial tools but also a range of freely available resources, including Atomic Red Team tests & Sigma analytics. Figure 4 highlights the resources discussed above (dark blue), plus two other simulation tests & detection analytics that cover variations on the reported Flax Typhoon behavior. These variations would allow the actor to achieve persistence via Sticky Keys and similar accessibility features, but they likely would not be detected with the Sigma rule logic highlighted earlier. There are of course myriad other persistence techniques, so defenders can start focusing on the Procedure that immediately matches a reported or observed one, then the most similar variations, and continue pivoting to account for even more alternatives as bandwidth allows.
Like this content? Check out our previous Community Edition pivoting demonstrations, focused on detections & simulations around recent ransomware and infostealer techniques.


